This article describes how to perform static analysis of suspicious file with use of a few tools like Oletools, IDA and RetDec.
Few weeks ago, an email with suspicious attachment had been sent to one of government agency in Poland. The attached file name is BG Presidency Draft Calendar-Final.doc.
SHA1 of the doc file is: 601367EED1DDC8473F99CAAA4E2673C13E5D30D7
The first step is to verify the content of the doc file. One of the tool which we usually use at Prevenity is Oletools. It is a package of python tools to analyse Microsoft OLE2 files.
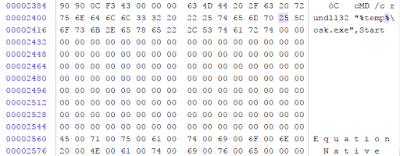
The RTFOBJ tool extracted for us ole objects. One of it (#2) contains command cMD /c rundll32 “%temp%\osk.exe”,Start. Now, we know that the entry point is the Start function from the osk.exe file (dll file).
We can also notice that class name for this object is Equation.3. The part of dumped object is presented below.
The exploit (CVE-2017-11882) used in this doc file is related to the executable module EQNDT32.EXE (Microsoft Equation Editor).
Note: We can easily confirm that Equation editor was used by analysing output from process monitor.
Let's come back to static analysis. The another OLE object (#0) is executable file, but it is the dll – not the exe file.
SHA1 of extracted dll file: D9276ED0D9370CE08970F869591E93185D3D022C
A few weeks ago Avast did great job by sharing the source code of the RetDec decompiler. Let’s use it to perform the initial analysis of our PE binary file.
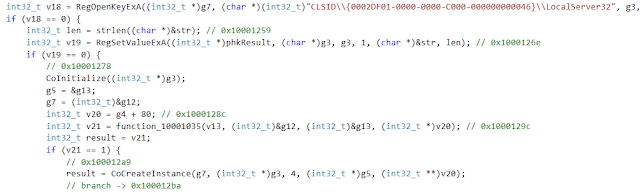
The first interesting notice is that the malware tries to hide communication with C&C by using COM technology. The COM allows malware developers to start and perform http communication with use of iexplore.exe process where the session is hidden. The malware is using a few interesting functions: CoInitialize() and CoCreateInstance(). The first is used to initialize the COM library. The second function is used to create an object of the class associated with a specified CLSID.
The registry value confirms that malware creates an instance of Internet Explorer.
The malware collects and then sends in HTTP GET to C&C server some basic information about an infected host like hostname, username and operating system type. This data are encrypted by using simple formula. Subtract 0x41 from current letter and XOR with counter.
The malware collects and then sends in HTTP GET to C&C server some basic information about an infected host like hostname, username and operating system type. This data are encrypted by using simple formula. Subtract 0x41 from current letter and XOR with counter.
Then such encrypted data are coded by Base64. The RetDec in comment provided information about identified base64 function.
The response from C&C server contains in body message a value parameter. The value of this parameter contains encrypted data (commands to execute) which must be decrypted by below code.
In next step malware tries to find the following characters „~~”. In this way commands from C&C server are extracted. Next few instructions are responsible for checking if command id contains only numbers between 0-9 and space as a separator.
We can identify few conditions which redirect code to execute commands, read files, delete files. All content sent to C&C server is encrypted by session symetric key.
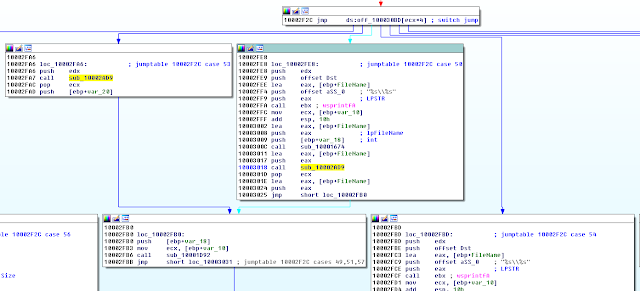
One of the feature is executing commands at compromised machines. The results are stores in fw1ei.tmp file.
As we can see wsprintfA() is used to prepare a final command. The first parameter of wsprintfA() is located a few lines above:
*(char *)(v3 | 2) = *(char *)((int32_t)"Cm" + 2);
By concatenating „Cm” with „D” malware builds command cmd and add destination executable file name received from C&C server.
Depending on command the result is sent to one of below URLs:
- http://%s/view.aspx?li=%s
- http://%s/post.aspx?fs=%s
- http://%s/li.aspx?id=%s
- http://%s/query.aspx?q=%s
Some IoC are presented below:
C&C server: maps.fakemediavis.com
IP address: 115.144.238.67
Created files:
- C:\Users\<username>\AppData\Roaming\mozilla\mozlib.dll
- C:\Users\<username>\AppDadta\Local\Temp\Microsoft Office Update.lnk with content: C:\Windows\system32\rundll32.exe C:\Users\IEUser\AppData\Roaming\mozilla\mozlib.dll,Start
- 601367EED1DDC8473F99CAAA4E2673C13E5D30D7
- D9276ED0D9370CE08970F869591E93185D3D022C
External links:








Brak komentarzy:
Prześlij komentarz